Python Forensics – Dshell and Scapy
Python Forensics – Dshell and Scapy
DShell
Dshell is a Python-based network forensics analysis toolkit. Developed by the U.S. Army Research Laboratory, this open-source toolkit was released in 2014. Its primary focus is to facilitate forensic investigations.
The toolkit consists of a number of decoders, listed in the table below.
| Sr. No. | Decoder Name and Description |
|---|---|
| 1 | dns This is used to extract DNS-related queries. |
| 2 | reservedips Identifies solutions to DNS issues. |
| 3 | large-flows Lists network flows. |
| 4 | rip-http Extracts files from HTTP traffic. |
| 5 | protocol Identifies non-standard protocols. |
The US Army Research Lab maintains a clone of the repository on GitHub. The link is as follows.
https://github.com/USArmyResearchLab/Dshell
This clone includes a script, install-ubuntu.py(), for installing the toolkit.
Once installed, it will automatically build the executable and dependencies, which will be used later.
Dependencies are as follows
dependencies = {
"Crypto": "crypto",
"dpkt": "dpkt",
"IPy": "ipy",
"pcap": "pypcap"
}
This toolkit can be used to work with pcap (packet capture) files, which are typically recorded during incidents or alerts. These pcap files are created by libpcap on Linux or WinPcap on Windows.
Scapy
Scapy is a Python-based tool for analyzing and manipulating network traffic. The following is a link to the Scapy toolkit –
http://www.secdev.org/projects/scapy/
This toolkit is used for analyzing and manipulating packets. It is very capable of decoding packets from a wide range of protocols and capturing them. Unlike the Dshell toolkit, Scapy provides investigators with detailed descriptions of network traffic. These descriptions are recorded in real time.
Scapy has the ability to perform profiling using third-party tools or operating system fingerprinting.
Consider the following example.
import scapy, GeoIP #Imports scapy and GeoIP toolkit
from scapy import *
geoIp = GeoIP.new(GeoIP.GEOIP_MEMORY_CACHE) #locates the Geo IP address
def locatePackage(pkg):
src = pkg.getlayer(IP).src #gets source IP address
dst = pkg.getlayer(IP).dst #gets destination IP address
srcCountry = geoIp.country_code_by_addr(src) #gets Country details of source
dstCountry = geoIp.country_code_by_addr(dst) #gets country details of destination
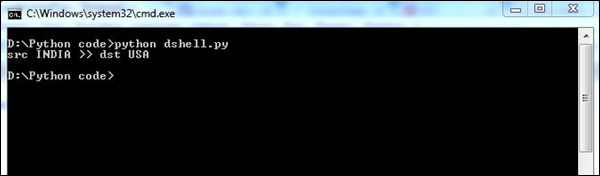
print src+"("+srcCountry+") >> "+dst+"("+dstCountry+")n"
This script gives a detailed description of the country details in the network packets they are communicating with each other.
The above script will produce the following output.